Defense in Depth
6 November 2025Developing systems that expose sensitive information on the internet requires us as developers and architects to think about security at all times. The classic model with only a strong perimeter defense is no longer suitable for modern architecture.
As a result of this our role has changed, and we need to shoulder a larger responsibility for the security of the applications and services we develop.
With the contents gathered on this page we describe what you need in order to build a system that is secure by design, with security controls in multiple layers according to the principles of defense in depth, least privilege and zero trust.
The contents are based on Omegapoint’s security research and collective experience building, operating and defending systems and organizations.
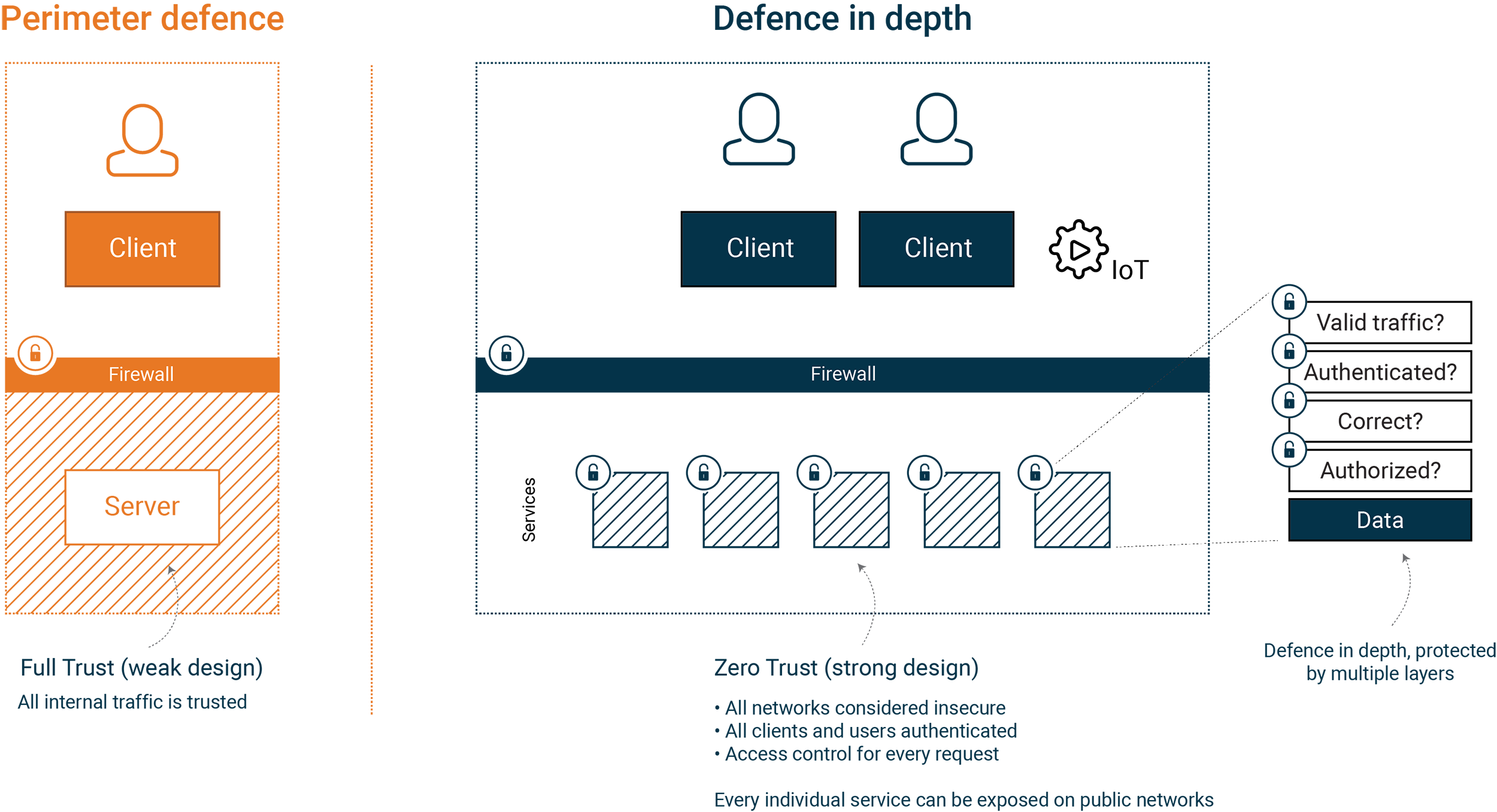
We recommend starting with the article on Secure Architecture which gives an overview of how these principles affect our architecture. It also sets the context for our seven part article series covering the following topics.
Further in-depth material based on the article series with code examples can be found here.
These articles are accompanied by implementations in Java and .NET. Source code repositories are available on Github at:
Defense in depth presentations
We also do presentations based on this content at international conferences. Recordings from some of them are available online:
Secure system integrations
Presented at NDC Security 2025 by Tobias Ahnoff (unfortunately this video freezes for 5 minutes).
Test driven application security
Presented at JFokus 2025 by Tobias Ahnoff and Erica Edholm.
OAuth2/OIDC security weaknesses and pitfalls
Presented at NDC Security 2024 by Tobias Ahnoff and Pontus Hanssen.
How to f*ck up at OAuth2 while following BCPs
Presented at Security Fest 2023 by Tobias Ahnoff and Pontus Hanssen.
Test driven application security
Presented at NDC Security 2023 by Tobias Ahnoff and Martin Altenstedt.
Defense in depth as Code
Presented at NDC Oslo 2021 by Tobias Ahnoff and Martin Altenstedt.
Implement defense in depth for your Java API:s
Presented at JFokus 2022 by Tobias Ahnoff and Erica Edholm.
Other media
The book “Secure by Design” https://www.manning.com/books/secure-by-design covers many of the Defense in Depth topics.